Google’s business applications development platform Apps Script is being abused by hackers to steal credit card information that customers use to shop online using e-commerce sites.
Google App Script
The script.google.com domain is used to successfully prevents malware scan engines from detecting their malicious activity and to bypass Content Security Policy (CSP) controls.
They use the fact that Google’s Apps Script domain would be regarded by on-line stores as trusted and potentially whitelist all Google subdomains within their sites’ CSP configuration (a security standard for blocking untrusted code execution in web apps).
Credit card skimmers are JavaScript-based scripts injected in web skimming (e-skimming) attacks by cybercrime groups known as Magecart groups into hacked online stores.
Once deployed, the scripts allow them to collect payment and personal information submitted by hacked shop customers and to collect it on servers under their control.
Google App Script domain used as an endpoint for exfiltration
This latest payment info theft strategy was discovered by security researcher Eric Brandel while reviewing the Early Breach Detection data provided by Sansec, a cybersecurity firm focusing on digital skimming.
Thanks to some data from @sansecio, I came across another example of a digital skimmer/#magecart script abusing a Google service for data exfiltration. In this case, the service being abused was Google Apps Script
— Eric Brandel (@AffableKraut) February 18, 2021
1/7 pic.twitter.com/xRzt29pD9L
This latest payment info theft strategy was discovered by security researcher Eric Brandel while reviewing the Early Breach Detection data provided by Sansec, a cybersecurity firm focusing on digital skimming.
As he found, the malicious and obfuscated skimmer script injected by attackers on e-commerce pages has captured payment information sent by users.
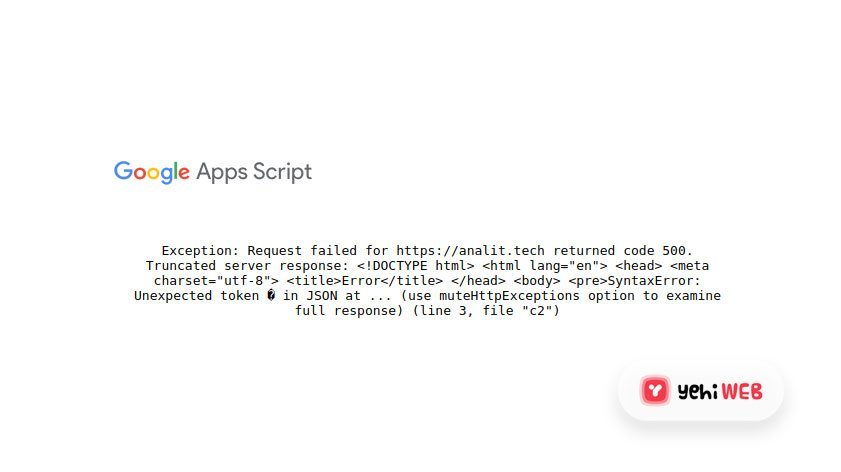
An exfiltration script google.com was used to transfer all the payment information stolen from the compromised online stores to the custom Google Apps script using the JSON base64 files.
After reaching the Google Apps Script endpoint, data was submitted to another server — analyst tech located in Israel — controlled by the hackers.
“The malware domain analit[.]tech was registered on the same day as previously discovered malware domains hotjar[.]host and pixelm[.]tech, who are also hosted on the same network,” Sansec said.
“E-commerce managers need to ensure that attackers cannot inject unauthorized code in the first place. Server-side malware and vulnerability monitoring are essential in any modern security policy.”
Google Analytics also abused to steal credit cards
Other Google services have also been exploited in Magecart attacks, with the Google Analytics tool being used by criminals to extract payment data from several dozen online retailers.
What made those attacks worse was that, by exploiting the Google Analytics API, the threat attackers could still bypass the CSP by seeing that the web stores whitelist Google’s web analytics service in their CSP configuration for tracking visitors.
As Sansec and PerimeterX discovered at the time, Google Analytics scripts allowed attackers to use them to steal and exfiltrate data instead of blocking injection-based attacks.
This was achieved by a web skimmer script specifically for encoding stolen data and distributing it in encrypted form to Google Analytics the attacker’s dashboard.
Based on the figures given by BuiltWith, more than 28 million pages are currently using Google’s GA web analytics services, with 17,000 of the websites accessible through HTTPArchive scanning in March 2020 whitelisting the google-analytics.com domain according to PerimeterX statistics.
“Typically, a digital skimmer (aka Magecart) runs on dodgy servers in tax havens, and its location reveals its nefarious intent,” Sansec explained at the time.
“But when a skimming campaign runs entirely on trusted Google servers, very few security systems will flag it as ‘suspicious.’ And more importantly, popular countermeasures like Content-Security-Policy (CSP) will not work when a site administrator trusts Google.”
“CSP was invented to limit the execution of untrusted code. But since pretty much everybody trusts Google, the model is flawed and faulty,” Sansec CEO and founder Willem de Groot explained.
Saad Shafqat
Related posts
New Articles
Whosvalora: Understanding the Digital Mystery That’s Taking Over Social Media
In the rapidly changing realm of internet culture, new terms and phenomena emerge almost daily. But few have captured the…